SonicWall Zero Day Exploits
We have just become aware of several recent zero-day exploits associated with SonicWall VPN appliances, this zero day has been exploited in the wild and has successfully sent ransomware to individuals globally who leverage this appliance model.
Priority:
This exploit has a CVSS score of 9.8 and considered critical in terms of establishing a remediation plan. It is recommended that if you have an affected model that you remediate within 24-48 hours via an emergency change.
The Vulnerability:
Vulnerability resulting in improper SQL command neutralization in the SonicWall SSLVPN SMA100 product allows remote exploitation for credential access by an unauthenticated attacker. This vulnerability impacts SMA100 build version 10.x.
The Remediation:
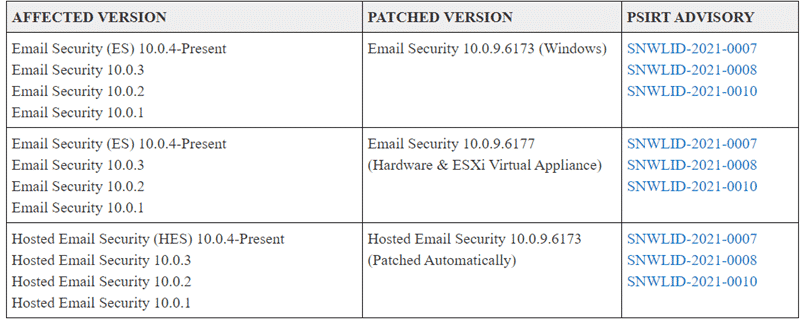
Patch the appliance to the current release:
The Workaround:
The following steps can be taken if you cannot currently patch your appliance:
- Enable multifactor authentication (MFA) as a safety measure.
- MFA has an invaluable safeguard against credential theft and is a key measure of good security posture.
- MFA is effective whether it is enabled on the appliance directly or on the directory service in your organization.
- Enable WAF on SMA100.
- Reset the passwords for any users who may have logged into the device via the web interface.
Reference:
- https://www.bleepingcomputer.com/news/security/sonicwall-warns-customers-to-patch-3-zero-days-exploited-in-the-wild/
- https://psirt.global.sonicwall.com/vuln-detail/SNWLID-2021-0001
- https://www.bleepingcomputer.com/news/security/new-ransomware-group-uses-sonicwall-zero-day-to-breach-networks/
- https://thehackernews.com/2021/04/hackers-exploit-sonicwall-zero-day-bug.html






